In this post we will learn how to reverse an app. Our target is reverseMe.exe and the application we are going to use is OllyDbg. To understand this post properly you must refer to the Revere Engineering : intro to Olly and Registers and Flags posts first.
Step 1
- Start Olly
- Open the reverseMe.exe file.
- Choose the cpu main thread window.
Step 2
- Now we need see what happens when we run the app, so press f9 or just click on the run button.
- The next thing we is the message box with the purchase error.
Step 3
- Now we need to restart the app, press the restart button from the toolbar (probably the second option on the toolbar).
- Now we will move on to each instruction and run each of them to see what exactly causes the message box to appear. We can do this by pressing f8, this will execute each instruction and move to the next one.
- Also our focus should be on the changes happening in different windows (specially the registers and flags).
- The black arrow points to the CMP instruction and the message.
- While executing each instruction one by one, we see a instruction whose corresponding comment is the error we see in the message box. A few lines above this instruction we see a CMP (compare) statement then a JNZ (jump on not zero) statement (if this CMP statement results into a zero then the jump does not take place and the next instruction is executed).
Now let us understand this CMP
statement. It is comparing the value in accumulator register (EAX) with -1. The value in EAX is -1 due the CALL
instruction just above the CMP statement. What the CALL instruction has done
is, it has checked for a file with the key of the app, and when the key did not
match it updated EAX to 1. The result of the CMP instruction is stored in the
flag Z. now if we wish to change the result of the CMP statement we can just
flip the value of Z (I guess this should do fine).
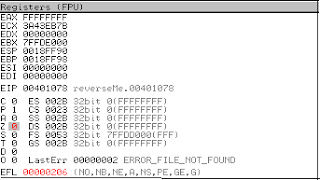
- The Register window, and the value of the Z flag has been flipped.
- Restart the app and reach the CMP instruction and then flip the Z flag and then continue the process of executing the app. Now we notice that the error is passed.
- We will continue the process of removing the reasons of failure, Next in the list we find a TEST instruction with a JNZ instruction, and just next to it this JNZ instruction gives us a hint that the reason might be the TEST instruction. A few instructions above the TEST instruction we see a PUSH instruction pushing the EAX in the stack and what’s now going to happen is comparing the values in the accumulator register and with a file that is going to be read in the next call.
The TEST instruction performs an AND operation between the
two inputs, this instruction also updates the value of Z, S, O flags (depending
upon the values of the two inputs).
- If the value of EAX is 0 the Z flag is in clear state. The JNZ instruction does not perform jump if the Z flag is in clear state (which in this case is not happening).
- The arrow points to the TEST instruction.
- What happens if this jump is avoided next comes the unconditional jump and this jump instruction results into the failure of the app.
- Now what we have to do is clear we have to pass this JMP instruction and this could be done if Z flag is in clear state. So make it happen.
- Notice the value of S flag it is zero before executing the TEST instruction. And the value of Z have been flipped.
- Now we are at the last lap of our run, we got to run each instruction again looking at the window we see there is JL instruction, for this JL instruction we have to update the S flag instead of Z. Now we have passed this, moving on with the same procedure leads us to the message box with the congratulation message.
- The value of S changes as soon as the Instruction is executed. We have to flip this to 0 to avoid the message box
- Let us run the app now we see the app running properly.
We
cannot always follow the same procedure (as it is very lengthy). So we need to
save the changes made in the app. We will learn this in the next post. Also We have many more procedures to reverse apps as this is very lengthy process so we will look at different procedures to do this in further posts.











Post a Comment