Following my past work, today I breached the "vulnbweb.com/'s" security using the 'Error based SQL injection'. I chose 'testasp.com/showforum.asp?id = 2' as my prey. First I checked exception handling of the web site, by putting a small quote after the 1 in the url(?id = 1'). Now the server responses with an error stating that the server being used is MYSQL, So this made me think a little then I got to the conclusion of using the Error based injection on this site.
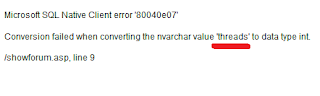
To get table name and column name from the table I used the SQL itself, I used the convert() function to produce an error and I will find the table name in this error. Using convert() function in the following way showed the error "id? = 1' and 1 = convert(int,(select top 1 from table_name from information_schema.tables )) #"
Following the same command I got to know the names of column and further the login information, like username and password.
The red line shows that the error produced by the convert command shows the name of the top one file name on the information schema. I found out the users table in the same way and the user details following the same method
To get table name and column name from the table I used the SQL itself, I used the convert() function to produce an error and I will find the table name in this error. Using convert() function in the following way showed the error "id? = 1' and 1 = convert(int,(select top 1 from table_name from information_schema.tables )) #"
Following the same command I got to know the names of column and further the login information, like username and password.







Post a Comment